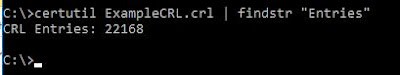
A certificate can be revoked for a number of reasons, and those are specified in the CRL as per RFC 5280 Section 5.3.1: CRLReason unspecified (0), keyCompromise (1), cACompromise (2), affiliationChanged (3), superseded (4), cessationOfOperation (5), certificateHold (6), removeFromCRL (8), privilegeWithdrawn (9), aACompromise (10) Value 7 is not used, removeFromCRL is only applicable to delta CRLs and certificateHold is a reversible revocation (can be "unrevoked" at a later stage). Please note that certificateHold is not an acceptable revocation reason in publicly trusted server certificates, as per CA/B Forum Baseline Requirements. https://tools.ietf.org/html/rfc5280#section-5.3.1 https://en.wikipedia.org/wiki/Certificate_revocation_list#Reasons_for_revocation https://cabforum.org/baseline-requir...