Cisco ISE CSRs and AD CS CAs
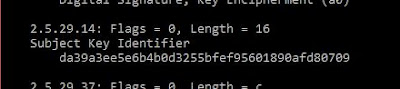
Cisco Identity Service Engine (ISE) devices for network authentication seem to have a "feature" that generates PKCS#10 CSRs with the SHA1 hash of an empty string in the Subject Key Identifier (SKI) extension:
da39a3ee5e6b4b0d3255bfef95601890afd80709
A Microsoft AD CS based Certification Authority, when presented with such a CSR, does not re-compute and overwrite the incorrect SKI extension included in the CSR but simply carries it over and adds it to the issued certificate:
It seems this is an issue that Microsoft have suffered from themselves:
https://crt.sh/?ski=da39a3ee5e6b4b0d3255bfef95601890afd80709
As per RFC 5280 the SKI value should be derived from the public key, but it is just an RFC 2119 SHOULD...
https://tools.ietf.org/html/rfc5280#section-4.2.1.2
https://www.ietf.org/rfc/rfc2119.txt
da39a3ee5e6b4b0d3255bfef95601890afd80709
A Microsoft AD CS based Certification Authority, when presented with such a CSR, does not re-compute and overwrite the incorrect SKI extension included in the CSR but simply carries it over and adds it to the issued certificate:
It seems this is an issue that Microsoft have suffered from themselves:
https://crt.sh/?ski=da39a3ee5e6b4b0d3255bfef95601890afd80709
As per RFC 5280 the SKI value should be derived from the public key, but it is just an RFC 2119 SHOULD...
https://tools.ietf.org/html/rfc5280#section-4.2.1.2
https://www.ietf.org/rfc/rfc2119.txt



Comments
Post a Comment