NDES with a standalone CA
Although generally considered insecure and lacking support for modern cryptography, the Simple Certificate Enrollment Protocol (SCEP) is still a widely used and supported protocol.
Microsoft's implementation of SCEP is the AD CS Network Device Enrollment Service (NDES), and one of the best deployment guides out there is Mark B. Cooper's "Securing and Hardening Network Device Enrollment Service for Microsoft Intune and System Center Configuration Manager" (from March 2015).
Within the NDES configuration recommendations checklist we can find the following:
"Dedicated Server Roles – The NDES service should be installed on a dedicated server. The Issuing CA should also be on its own dedicated server."
which makes a lot of sense but unfortunately is not always possible.
Depending on the use case for the end entity certificates issued via SCEP, in many cases it will make sense to issue them from a standalone CA, to avoid it being trusted in Active Directory. If certain lack of control regarding certificates issued via SCEP is understood as being a risk, and there is no reason for those certificates to be trusted across the domain, a standalone CA might be the safest choice.
The choice of a Standalone CA vs. an Enterprise CA comes with strings attached, such as e.g. certificate templates not being available, but a pretty much undocumented side effect is that such a choice also has an impact in the deployment architecture.
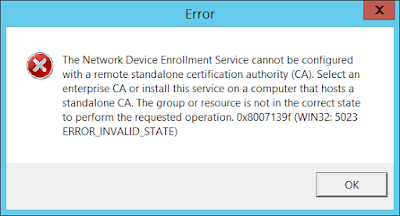
Once a standalone CA is deployed on a dedicated server we proceed to install the NDES service on another dedicated server, but when configuring it, as we specify a CA in a remote server within the "CA for NDES" configuration step...
0x8007139f (WIN32: 5023 ERROR_INVALID_STATE)
When using a Standalone CA to issue certificates via SCEP the NDES service must be installed in the same server where the CA is installed.


Do you have an AD Infrastructure?
ReplyDeleteAD infrastructure is optional, a standalone CA can be installed on a server member of a domain or a workgroup (without AD).
DeleteThe concern highlighted as a reason to choose a standalone CA setup instead of an enterprise (AD integrated) CA is the fact that enterprise CAs are by default trusted across the domain, which is not always the desired outcome.
The constraint regarding both NDES and CA roles having to be installed on the same server applies regardless of whether the server is a domain member or not.
Hi Do we need a CA templates for the deployment?
ReplyDeleteStandalone CAs don't support templates, that's an enterprise CA feature since templates are stored in AD.
DeleteTemplates are therefore not required, the certificate profiles for the NDES service (Registration Authority - RA) certificates are built into the role and will be generated as part of the role configuration without the need for any AD based certificate templates. The outcome is the same as using the "Exchange Enrollment Agent (Offline Request)" and "CEP Encryption" templates in an installation using an enterprise CA.
The lack of templates does introduce certain level of complexity when it comes to renewing the RA certificates, though, since the requests have to be manually crafted.
More importantly the lack of templates has an impact on the requests raised via SCEP, since those can't be mapped to a template and constrained accordingly.